- Home
- ProductsBackAI Powered Automations
Intelligent automation for compliance tasks
BackPolicy AgentRisk AgentVendor AgentAI CISO (Coming Soon)Compliance CoreEnd-to-end compliance management
BackCompliance EngineControls ManagementAutomated EvidenceIntegrations (450+)Policy ManagementAudit CenterFindings & Corrective ActionsThird-Party ManagementManage external risk effectively
BackData Sub-processor ManagementSupply Chain Attack Surface MonitoringAI Agent - Security QuestionnaireAdditional SolutionsSpecialized tools to enhance your compliance program
User Access ManagementManage external risk effectively
Risk ManagementIdentify and mitigate compliance risks.
TrainingsShowcase your security posture
Trust CenterShowcase your security posture
- FrameworksBackFramework & RegulationsSOC 2
SOC 2 defines criteria for managing customer data based on five trust service principles.
ISO 27001 (ISMS)ISO 27001 requires establishing, implementing, and maintaining a comprehensive information security management system.
HIPAAHIPAA establishes standards for protecting sensitive patient health information with requirements for data privacy, security provisions, and breach notifications.
GDPRGDPR enforces strict data protection regulations for organizations operating in the EU, requiring consent, transparency, and giving individuals control over their personal data.
Australian Privacy Principle (APP)APPs outline how Australian organizations must handle, use, and manage personal information, covering collection, use, disclosure, and data security requirements.
Any Custom FrameworkCreate and implement customized compliance frameworks tailored to your specific industry requirements, internal policies, or regional regulations.
Integrations.webp) 400+ Integrations
400+ IntegrationsAutomatically collect evidence and monitor compliance with current and upcoming integrations.
- Pricing
- ResourcesBackBlog
Explore Our Blog, Insights, News, and More
Help CenterAccess comprehensive guides, tutorials, and FAQs to maximize your compliance automation journey and resolve common questions quickly.
Free ToolsExplore our collection of complimentary compliance resources, templates, and self-assessment tools to strengthen your security posture.
- CompanyBackCompanyAbout Us
We make compliance accessible to companies of all sizes without the traditional headaches and costs.
Our PartnersWe've built a global network of trusted partners to help you achieve and maintain compliance efficiently.
CareersExplore opportunities to work with a team passionate about making security accessible to all businesses.
Contact UsConnect with our team for guidance on your compliance path.
Trust CenterReview our security practices, certifications, and compliance commitments that safeguard your data and demonstrate our dedication to trustworthiness.
ISO 27001 vs SOC 2 (2025): Which Should You Do First?

- Mostly selling in the US? Start with SOC 2. Ship Type I fast, then roll into Type II.
- Selling globally or into regulated sectors? Go ISO 27001 first for the certificate buyers recognize.
- Need both? Plan a phased roadmap and reuse the same evidence so you don’t do the work twice.
You’ll hit this fork sooner than you think: ISO 27001 vs SOC 2. Both tell customers you take security seriously, but they do it in different ways. SOC 2 is a CPA attestation against the Trust Services Criteria. ISO 27001 is an international certification of your ISMS by an accredited body. In 2025 the call usually comes down to where the revenue lives and how quickly you need proof.
Here’s the deal: US-first pipeline? SOC 2 is often the shortest path to “yes.” Building credibility across Europe, APAC, or regulated industries? ISO 27001 lands better. And if you’ll need both within the year, we’ll show you how to sequence them and reuse artifacts—risk register, policies, access reviews—so you move faster without doubling effort. By the end, you’ll know which to do first and how to make the second one easier. Sounds simple, right? Let’s make it that way.
ISO 27001 vs SOC 2 at a Glance
What is SOC 2?
SOC 2 is an independent attestation performed by a CPA firm against the Trust Services Criteria: Security (required), plus optional Availability, Confidentiality, Processing Integrity, and Privacy.
- Type I looks at control design at a point in time.
- Type II evaluates operating effectiveness across a period (commonly 3–12 months).
You walk away with a narrative report you can share under NDA. It’s the US enterprise comfort blanket.
What is ISO 27001?
ISO/IEC 27001 certifies your ISMS—the system that governs risks, policies, and controls. You align controls via your Statement of Applicability, referencing Annex A (93 controls), then complete Stage 1 and Stage 2 audits with an accredited certification body.
You earn an internationally recognized certificate on a three-year cycle, with annual surveillance. Think of it as your global passport.
Key Differences That Matter to Buyers
Deliverable — Report vs Certificate
- SOC 2: an AICPA-style attestation report (Type I/II). US buyers ask for it by name.
- ISO 27001: a formal certificate many global procurement teams are trained to look for.
Scope & Control Model — TSC vs Annex A (93)
- SOC 2 lets you pick criteria beyond Security, which gives you scope flexibility.
- ISO 27001 expects a documented ISMS with real governance: risks, owners, SOPs, logs, and an SoA explaining what’s in and why. Less wiggle room, more structure.
Audit Cadence — Type I/II vs Stage 1/2 + Surveillance
- SOC 2: renew annually; Type II covers an operating period.
- ISO 27001: 3-year certification with annual surveillance, then recertification.
Regional Recognition — US vs Global
- SOC 2: the de-facto US ask for SaaS and cloud vendors.
- ISO 27001: global signal, especially in EMEA/APAC and regulated sectors.
Buyer Signals & Procurement Realities in 2025
Security asks aren’t random; they’re shortcuts for trust. Here’s how they show up in real deals.
RFP language & checklists. US buyers often write “Provide your SOC 2 Type II report (current).” Outside the US, you’ll see “Provide your ISO/IEC 27001 certificate and scope statement.” Neither is a trick—they’re proxies for two different trust models: operational evidence over time (SOC 2) vs formal management system certification (ISO 27001).
Stakeholders. In fast-moving SaaS sales, the security reviewer is rarely a full-time auditor. They’re a senior engineer, IT lead, or procurement analyst with a checklist. Their job is to reduce risk quickly. If US-based, a SOC 2 pdf under NDA often closes the loop. If global or regulated, ISO 27001 is the signal they know how to interpret with minimal back-and-forth.
Timing. A common failure mode: waiting until the final mile of a deal to start. Buyers can’t bend their governance for you. If you’re US-first, ship Type I early as a conversation starter, then promise the Type II window on a clear timeline. If you’re global, show the Stage 2 audit date on the calendar so procurement sees momentum, not intent.
Trust extras that tip the scale. A light Trust Center with human-readable policies, incident contacts, uptime, and sub-processors smooths reviews. So do evidence teasers: anonymized screenshots of log retention, MFA policies, access review results. These aren’t substitutes for SOC 2/ISO—but they shorten cycles when the paperwork takes time.
Bottom line: buyers want a credible, verifiable signal. Give them the one they’re primed to accept, plus a small package of proof that you’re not window-dressing.
Timelines & Costs in 2025

SOC 2 Type I/II — prep windows & renewal
Type I is the fast on-ramp—many teams get there in 1–3 months once gaps are closed. Type II usually runs 3–12 months to gather evidence across the period, then audit. Keep a steady drumbeat on access reviews, logging, and tickets so renewals don’t become fire drills.
ISO 27001 — Stage 1/2, surveillance, recertification
Focused teams often reach readiness in 3–6 months. You’ll complete Stage 1 (documentation/readiness) and Stage 2 (implementation/effectiveness). You get certified, then pass surveillance audits each year, with a recert at year three. It’s durable governance, not just paperwork.
Cost drivers & ways to avoid overruns
Drivers: scope breadth, control maturity, integrations, headcount, and (for SOC 2) extra criteria beyond Security.
How to save: right-size your scope, automate evidence capture (access reviews, vuln scans, log retention), and reuse shared artifacts across both frameworks. Small move, big payoff.
Which Should You Do First? (Decision Paths)
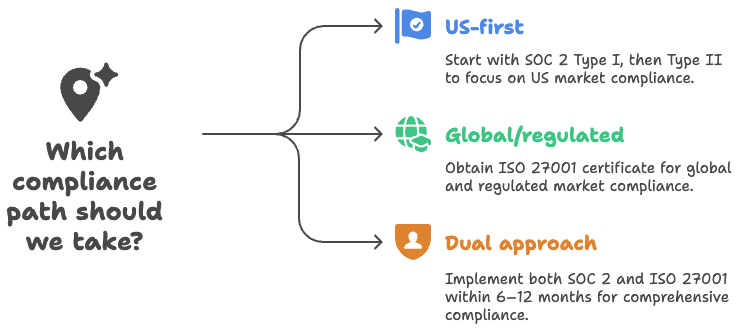
US-first SaaS → SOC 2 first (Type I → Type II)
If ~80% of your pipeline is US, ship SOC 2 first. Land Type I fast for credibility, then slide into Type II for stronger proof. Build policies, a risk register, and monitoring with ISO-friendly structure so you can pivot smoothly later.
Global/regulated → ISO 27001 first
Selling across EU/APAC or into finance/health/gov? ISO 27001 is a better opener. Procurement teams know it, and partner programs often expect it. You’ll still be in a great spot to add SOC 2 using the same evidence base.
Cross-border growth → Phased/parallel plan (6–12 months)
Need both soon? Do this:
- Stand up ISMS foundations once (risk, policies, asset inventory, vendor risk, access reviews).
- Pick the first external audit based on near-term revenue (SOC 2 Type I or ISO Stage 2).
- Backfill the second standard with a mapped delta—not a second project.
Scenario Deep Dives (What this looks like in the wild)
A) US-heavy pipeline, mid-market SaaS (sales tooling).
Your top 20 prospects are US-based and already ask for SOC 2 in security forms. You run a 30-day hardening sprint (MFA, logging, access reviews, vendor risk), push a Type I audit, and publish a short Trust Center. You book Type II for a 6-month window. Deals unblock because buyers can see real dates and a fresh report is coming. Nine months later, you reuse the same evidence base to kick off ISO 27001 without re-inventing your program.
B) Global fintech integration partner program.
Partner docs call for ISO 27001 with an explicit scope statement. You stand up the ISMS once: risk register, SoA, policies/SOPs, inventories, vendor reviews, and monitoring. You pass Stage 2, then maintain surveillance. Six months in, one US prospect insists on SOC 2. No panic—you already have access reviews, tickets, logs, and change records. You map them to the Trust Services Criteria and complete a Type I quickly, then slot a Type II period that overlaps your ISO surveillance cadence.
C) Cross-border SaaS with looming enterprise pilots.
You’ll need both inside a year. You start by standing up shared foundations (risk, policies, asset inventory, vendor risk, access controls, vulnerability management). You choose the first external audit based on the earliest high-value pilot (SOC 2 Type I or ISO Stage 2). While that’s underway, you build the delta for the second standard in parallel. The outcome: two credible badges in under 12 months without running two separate programs.
D) Early-stage team <25, light security history.
You focus on the smallest cohesive scope (single product, single region, single tenant). You document what you actually do, not what you wish you did. You implement real logging/alerting (not just enabled features), prove MFA everywhere, and run your first access review. With the basics clean, either SOC 2 Type I or ISO Stage 2 is achievable—then you scale the scope as deals demand it.
A Practical 90-Day Action Plan (Pick SOC 2-first or ISO-first)
Days 1–15 — Foundation & scope.
- Lock scope (product, region, data flows).
- Draft policies that match reality (access, change, incident, vendor, logging).
- Build your asset inventory and data classification.
- Stand up MFA, SSO, role-based access, and log retention targets.
Days 16–45 — Evidence engine.
- Start access reviews (privileged + sample users).
- Turn on actionable alerting (failed logins, admin changes, anomalous activity).
- Run vulnerability scans and create a simple patch SLA.
- Centralize tickets/approvals for change and vendor onboarding.
- Draft your risk register with owners and treatment plans.
Days 46–75 — Pre-audit hardening.
- Close quick wins from findings (MFA gaps, stale access, high vulns).
- Finish SoA draft (ISO) or criteria mapping (SOC 2).
- Dry-run an incident tabletop and record lessons learned.
- Publish a basic Trust Center with non-sensitive info.
Days 76–90 — Audit window.
- SOC 2-first: perform a readiness review → Type I.
- ISO-first: complete Stage 1, address deltas, then Stage 2.
- Book your renewal cadence (Type II period or surveillance dates) so you never scramble again.
Pro tip: One owner, one source of truth for evidence, and weekly 30-minute checkpoints. That rhythm alone saves weeks.
Doing Both Without Doubling Work
Evidence you can reuse
- Risk register (method, owners, treatment plans)
- Policies & SOPs (access, vendor, change, incident, logging/monitoring)
- Asset inventory & data classification
- Access reviews (JML, privileged access, SSO/MFA)
- Vulnerability management (scans, patch SLAs, exceptions)
- Vendor risk management (questionnaires, contracts, SIG/CAIQ if used)
- Security awareness training (completion records)
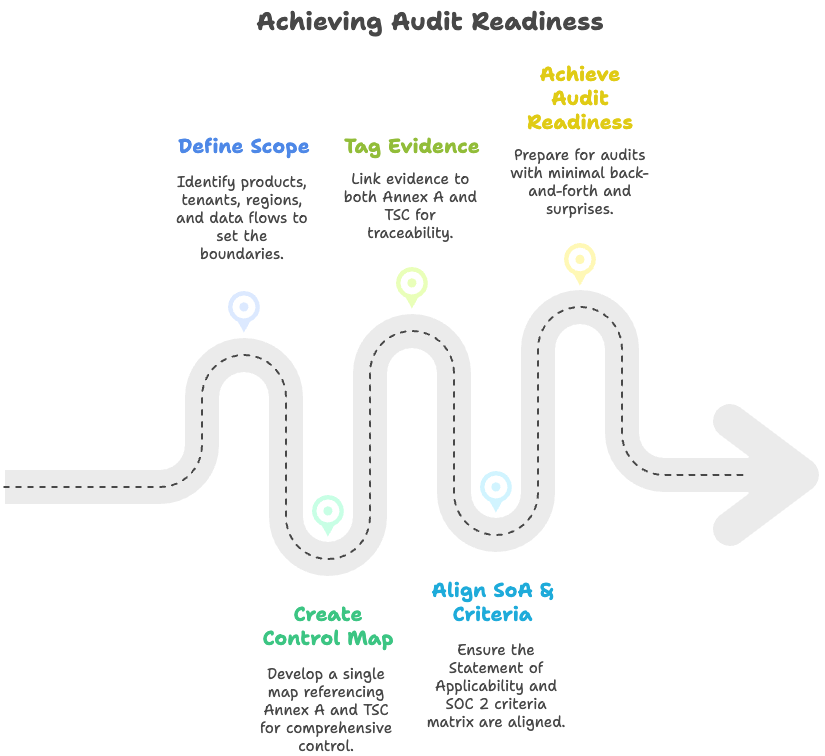
Mapping mindset & scope hygiene
Start with scope: products, tenants, regions, data flows. Keep a single control map that references Annex A and the TSC. Tag evidence to both. Keep your SoA and SOC 2 criteria matrix aligned so auditors can follow the thread. Less back-and-forth, fewer surprises.
Common Pitfalls & How to Avoid Them
Over-scoping & policy bloat
Tighten the perimeter. Write short, actionable policies backed by real SOPs and logs. If your policy reads like a novella, it’ll rot—and auditors can tell.
Weak evidence hygiene & log coverage gaps
Centralize evidence. Enforce MFA everywhere, ensure alerting is real (not just enabled), and keep retention long enough to cover your Type II period. Future-you will thank you.
Third-party/vendor risk blind spots
Track critical vendors, DPAs, sub-processor lists, and attestations. Run periodic reviews and chase remediation when signals turn red. It’s cheaper than a surprise during due diligence.
FAQ
- Is ISO 27001 harder than SOC 2?
Different shape, similar effort. ISO 27001 is more program-heavy (governance, SoA, surveillance). SOC 2 is evidence-heavy over time (Type II). Your maturity decides which feels tougher. - How long does SOC 2 Type II vs ISO 27001 take?
Many teams hit SOC 2 Type I in 1–3 months, then Type II after 3–12 months of operating evidence. ISO 27001 readiness often lands in 3–6 months, then Stage 1/2 and ongoing surveillance. - Do we need both for enterprise deals?
If you sell globally or into mixed markets, probably yes—eventually. US-heavy pipelines usually start with SOC 2; global or regulated pipelines get more lift from ISO 27001 first. - Who audits each?
SOC 2: licensed CPA firms. ISO 27001: accredited certification bodies (check IAF accreditation to avoid pushback). - How long are they valid?
SOC 2: the report reflects a point or period; buyers expect annual refresh. ISO 27001: 3-year certification with annual surveillance. - Can we share our SOC 2 publicly?
Most teams share SOC 2 under NDA because reports include sensitive system details. Your Trust Center can describe scope and the period covered, then handle access via request flow. - Does ISO 27001 replace SOC 2 (or vice-versa)?
No. They signal different things to different buyers. ISO 27001 shows a certified management system; SOC 2 proves operating effectiveness over time. If your market spans US and global buyers, you’ll likely want both. - Where do AI/ML and cloud specifics fit in 2025?
Not a separate badge (yet). They live inside the same controls: access, monitoring, data protection, vendor risk, change management. Document model/data access, training data lineage, and third-party AI services like any other critical asset—auditors will ask.
Wrap-Up
Here’s the simple play: match your first step to where deals are blocked. If you’re US-centric, grab SOC 2 Type I to open doors and build toward Type II without drama. If you’re chasing global or regulated buyers, ISO 27001 sets a sturdier foundation and carries farther in procurement. And if you’ll need both, plan a phased route and reuse the same evidence so your second audit feels like a guided tour, not a second mountain.
Quick Re-cap
- Choose the first standard by pipeline geography and buyer expectations.
- Build ISMS foundations once; map controls to both standards from day one.
- Keep scopes lean, automate evidence, and skip policy theatre.
Book a 15-min demo to see how we automate evidence collection and mapping.
External authorities
- ISO/IEC 27001 overview: https://www.iso.org/standard/27001
- AICPA SOC 2 overview: https://www.aicpa-cima.com/topic/audit-assurance/audit-and-assurance-greater-than-soc-2
- IAF accreditation basics: https://iaf.nu/en/home/
.svg)

.webp)